[Alibaba Cloud Thailand] Encrypting Cloud Data with Alibaba Cloud
By Saris Kongpichetkul, Presales Engineer of ATCETERA CORPORATION LIMITED and partner of Alibaba Cloud Thailand
What Is Cloud Encryption?
Before transferring data to the cloud for storage, cloud storage providers encrypt the data. On the cloud, encryption may range from encrypted connections to limited encryption of specific data (like account credentials) to full end-to-end encryption of all data uploaded to the cloud. This type of model encrypts data as soon as it is received, providing encryption keys to customers so they can safely decrypt data as required.
A system, database, or file that has been encrypted cannot be decoded without its decryption key, making it one of the most secure approaches to data security. Companies can secure sensitive data by encrypting and managing encryption keys securely. Without its key, encrypted data is essentially unreadable and meaningless even if it is lost, stolen, or accessed without authorization.
Challenges Associated with Cloud Encryption
Despite its effectiveness in bolstering data security, encryption is generally underused, which is perhaps one of the primary challenges it faces. Businesses of all sizes are relying on cloud services increasingly to improve compliance and efficiency while maintaining security.
Cloud storage providers incur costs associated with encryption since encrypting data requires additional bandwidth. Thus, some cloud storage providers limit their cloud encryption services, while others encrypt their data on-premises before storing it on the cloud. This is an approach that some customers choose because it saves costs while allowing them to keep control over their encryption keys and the entire encryption process within their network, only transferring encrypted data to the cloud once it has been encrypted.
Alibaba Cloud Data Encryption Service can overcome these challenges. This service gives Alibaba Cloud customers access to hardware security modules (HSMs) hosted on the cloud. Cryptographic operations are processed by HSMs, and keys are stored in them securely.
A Few of the Features the Data Encryption Service Provides to HSMs
- A secure method of generating random numbers
- Hash-based message authentication codes (HMACs) support multiple digest algorithms.
- Implement key lifecycle management functions, such as key creation, destruction, import, and export
- Sign and verify asymmetric keys
- Multi-key support
- Data encryption and decryption can be done with symmetric and asymmetric keys.
Alibaba Cloud Data Encryption Service Architecture
Alibaba Cloud is a hosted service that offers cloud data encryption. Alibaba Cloud makes it easy and cost-effective to deploy this service since they manage and maintain the HSMs.
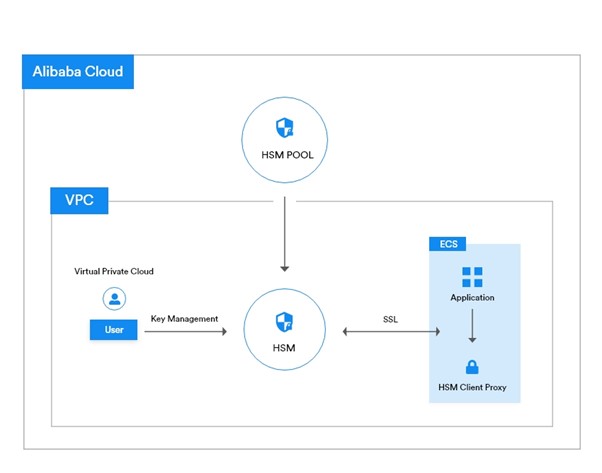
Fig: Architecture of Alibaba Cloud Data Encryption Service
An Overview of Alibaba Cloud Data Encryption Benefits
- Cybersecurity
- Maintaining Compliance
- Transparency
- Reduction of Risk
- A Commitment to Complete Protection of Data
- Protection of Personal Information
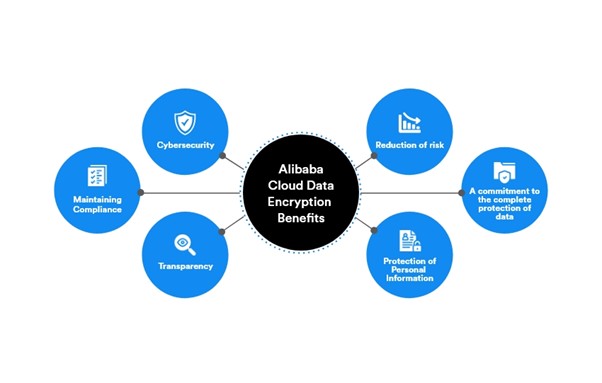
Fig: Benefits of Alibaba Cloud Data Encryption Service
The following scenarios illustrate how Alibaba Cloud Data Encryption Service can be used:
Users of the Data Encryption Service can leverage the HSM to perform operations, such as offloading SSL and TLS handling for your web servers, protecting the private key for your certificate authority (CA), and encrypting sensitive data in your cloud applications with Transparent Data Encryption (TDE).
- A security measure that protects sensitive data is encryption.
To meet security and compliance requests, sensitive data can be encrypted by integrating the HSMs with your applications that do business in public services, e-commerce, financial services, and other businesses.
- Integrating Oracle TDE
Transparent Data Encryption (TDE) provides a mechanism for protecting sensitive data by encrypting sensitive data in database columns or operating system file tablespaces. A security module outside the database stores encryption keys to prevent unauthorized decryption. Data files can be encrypted in TDE to prevent operating systems from accessing sensitive data.
- HTTPS Websites with SSL Offloading
Public-private key pairs and public key certificates enable HTTPS websites to establish secure connections with clients. This method consumes a great deal of web server resources, cuts down on webserver availability, and reduces web server efficiency. The SSL certificate private key file is stored on the disk, and it is at risk of being compromised. You can generate private keys and complete SSL offloading through HSMs on the Alibaba Cloud Data Encryption Service.
- Issuing the CA private keys should be protected
Certificate authorities (CAs) are responsible for issuing digital certificates. The CA private key is used to sign digital certificates, certifying ownership of public keys by the named subject. A digital certificate proves the owner of a public key is the subject of the certificate. The private key must be stored in an HSM, and cryptographic operations must be performed using an HSM.
Final Thoughts
Standards, regulations, and organizations’ security needs make cloud encryption a necessity, despite the challenges and cons. Cloud encryption is considered a crucial approach to protecting information by security experts. Additionally, Alibaba Cloud providers offer several different encryption applications that meet a wide range of budgets and data protection requirements. Organizations should be aware of their data protection needs and use Alibaba Cloud Data Encryption Services to avoid putting the business at risk and take advantage of cloud encryption.

